Privileged Container
This finding indicates that a privileged container with root level access was launched on your Kubernetes cluster.
To simulate the finding we'll apply the following yaml.
/workspace/modules/security/Guardduty/privileged/privileged-pod-example.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: ubuntu-privileged
spec:
selector:
matchLabels:
app: ubuntu-privileged
replicas: 1
template:
metadata:
labels:
app: ubuntu-privileged
spec:
containers:
- name: ubuntu-privileged
image: ubuntu
ports:
- containerPort: 22
securityContext:
privileged: true
Create the deployment by running the following command.
~$kubectl apply -f /workspace/modules/security/Guardduty/privileged/privileged-pod-example.yaml
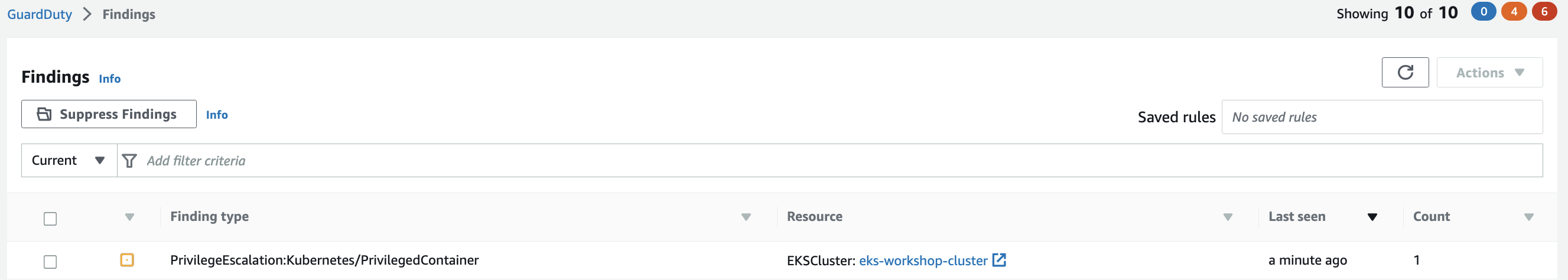
Within a few minutes we'll see the finding PrivilegeEscalation:Kubernetes/PrivilegedContainer in the GuardDuty portal.
Cleanup:
~$kubectl delete -f /workspace/modules/security/Guardduty/privileged/privileged-pod-example.yaml